Hi, what are you looking for?
- Home
- News
- Tech

Indonesia Blocks Elon Musk’s Grok Over Deepfake Concerns

Dutch Court Voids AI-Generated Wedding Vows, Invalidates Marriage

NCC, CBN Finalize 30-Second Refund Rule for Failed Airtime, Data Buys

West Africa readies for largest blockchain gathering as Ibom Blockchain Xperience sets March 2026 date

MENXTT NG to pre-install Bitdefender Antivirus on all laptops from 2026
- Entertainment

End of an Era as Multichoice Delists from JSE After Canal+ Takeover

From Streams to Streets: Spotify Wrapped 2025 Takes Africa on a Real-World Road Trip

Netflix Seals $82.7bn Deal to Acquire Warner Bros., HBO Max

GoodGirl LA takes the throne as Spotify’s Equal Africa Ambassador for November

Nissi named Spotify’s EQUAL Africa Ambassador for October 2025
- Sports

NIS DG Shaibu Accuses FG of Deliberate Exclusion from Sports Funding Despite Record Budgets

Chelsea, Maresca Part Ways After 18 Months

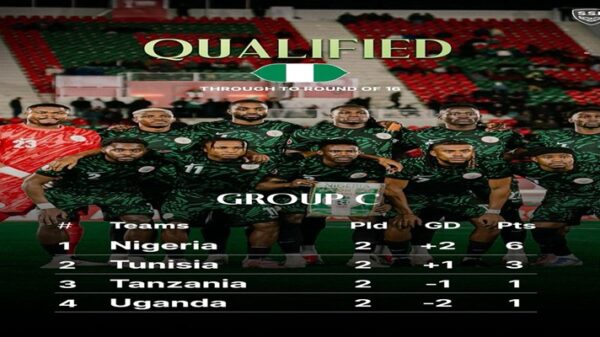
Super Eagles of Nigeria beat Tunisia 3-2 to qualify for AFCON Round of 16

FG fulfils housing, land pledges to Super Eagles for 2023 AFCON feat

AFCON 2025 winner to earn $10m as CAF hikes prize money
- Politics

FG Weaponising EFCC Against Me for Rejecting APC – Bauchi Governor

Only Fresh Passage, Not Re-Gazetting Can Validate Tax Reform Laws – Atiku

Tinubu announces arrival of 4 US attack helicopters

Tinubu Confident State Police Will Be Achieved, Reaffirms Local Government Autonomy

Former Delta Senator Peter Nwaoboshi Dies at 68
- Business

FCCPC Secures Compliance, Unseals Ikeja Electric HQ After Consumer Rights Enforcement

JustMarkets Launches Global Boost Contest With Gold Prizes for Traders

CAC to Shut Down Unregistered PoS Operators by January 2026

Konga Extends Yakata Sale to December 6 Following Overwhelming Customer Demand

MAKEMS 2025 Jewelry Exhibition in Abuja Holds on Saturday